Data protection in a world of genetic mutations
This article uses lessons learned from the natural world to describe the problems faced by IT teams around the globe when it comes to malware. We also propose new strategies and tactics to deal with data protection(for Linux, Windows, Mac, Solaris, AIX) since traditional backups have failed to get everything back on time.
A world in turmoil
The world is in turmoil. Risky events, natural disasters, ransomware, malware and other causes of data loss are increasing in frequency, intensity and in duration.
For example, the city of Atlanta has not recovered completely yet, from the cryptomalware that crippled many of its systems in March. The city of Baltimore’s emergency dispatch system and its 911 and other emergency systems were also brought down for 17 hours. Denver’s numerous systems and 911 infrastructure were targeted and downed for a significant amount of time. So was Colorado’s department of transportation. The cities of Hinesville, GA, Spring Hill, TN and many more have been all devastated in the past few months alone.
Soft Targets
The victims and the target of attacks are diverse. Many industries were also targeted. Some examples of targets include:
- Government Agencies
- Technology companies
- Healthcare companies
- Retail
- Manufacturing, etc.
Nothing is sacred or is safe any more
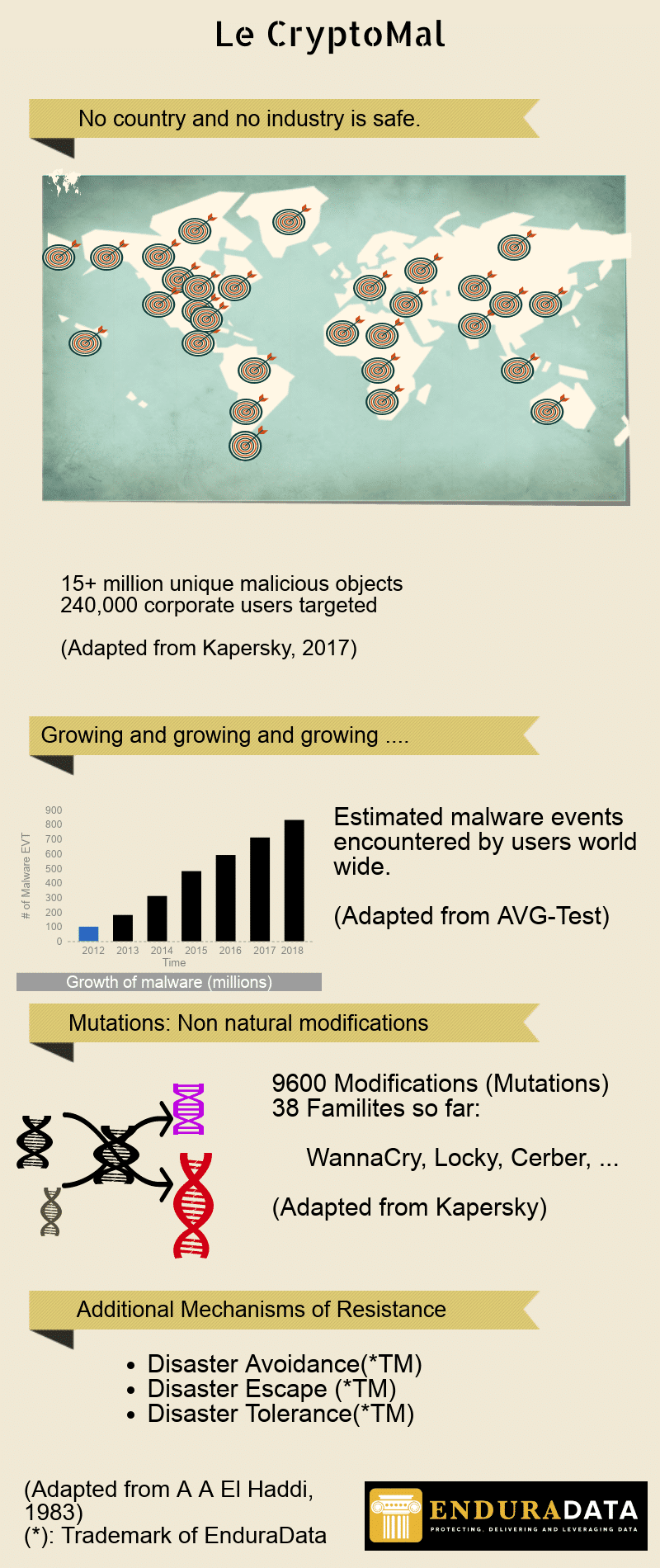
Cyber attacks affected 75% of Healthcare companies in one way or another[1].
57% of attacks targeted large companies [1 ] with over 240,000 corporate users infected (2) and distributed over 939,722 computers (2). 29.4% of computer users had experienced at least one attack from over 15 million unique malware objects out there in the etherland.
To make matters worse, the malware continues to mutate through continuous code, targets and payload delivery changes (just like genetic mutations, to improve the potency of the deadly cyber weapons). As of this writing, there are over 38 families of these harmful ransomware objects roaming the world’s IT ecosystems(WannaCry, Locky, Cerber, ….)[2].
When I gave a talk about cryptolocker back in 2013, I expected the varieties and new hybrids to be stable over longer periods of times. Instead, we are now thousands of generations away from time T0 when the first man induced adaptation/mutation took place and F1 was released to system farms. Consequently, generation F2 is deadlier than F1 and F1000 is deadlier than all preceding generations (Technically if we used non genomic discarding). Hence the yield and effects of new alleles will continue to rise. Unfortunately this is not the green revolution imagined by the Nobel Norm Borlaug, nor is it something Mendelian inheritance could have explained due to the nature of most software and its malleability.
The growth, frequency and intensity
In 2017, we examined the growth rate of “les CryptoMaux”(Le Mal in French: means bad! plural is les Maux) and found rates moving exponentially at 300% ( https://www.enduradata.com/the-rise-of-ransomware-backup-and-protect-your-data-before-you-are-forced-to-pay-up/). A few months later we are seeing data indicating a jump from 4000 incidents per day to 250K/day[2]. Epidemiologists and the world health organization (WHO) would have raised alarms if these were human infections ( Don’t blame me if I suggest creating a new UN organization called World Systems Health Organization: WSHO, something with more resources and teeth than CERT).
The intensity and the cost
The real cost is not what the victims will pay to get (or not get the keys) the data back. The devastation, loss of productivity, economic profits, lives and reputations outweigh the ransom. The recovery efforts are enormous and the post recovery impacts on organizational changes that follow are huge. We looked at this in our “Aftermath of Wannacry” in our blog months ago (“https://www.enduradata.com/aftermath-wannacry-ransomware”) and the costs continue to mount without bounds.
We re-visited the costs in the “real costs of data loss article” (https://www.enduradata.com/real-costs-of-data-loss-imperfect-backups).
In monetary terms, it is hard to quantify, but we have seen numbers ranging from $700,000 to $56 millions per hit. If recent history is a benchmark, costs will only continue to soar and the number of soft targets will continue to go up. As of this writing, I did not see any statistics about deaths or severe effects on the health of patients yet.
I believe that we must combine various tactics and strategies to protect important data wherever and whatever it is.
Thinking about antidotes and disaster recovery strategies
We believe that we must use some lessons we’ve learned from ecosystems, the natural world and the natural sciences to protect all digital assets and have effective disaster recovery strategies. Systems staff and management must consider the following:
- Disaster avoidance (TM) [3]
- Disaster Escape (TM) [3]
- Disaster tolerance (TM) [3]
However, more methods, tools and policies must be used to protect digital assets. We urge the reader to consult the following external resources as well.
https://www.enduradata.com/resources-related-to-data-protection/
About EnduraData
EDpCloud is a data replication software solution for data protection, end point backup, disaster tolerance, avoidance and escape.
EDpCloud is an enterprise cross-platform file replication solution. IT staff use it to:
- Mirror files from many locations to a single locations
- Synchronize and replicate data in real-time, on demand or at various intervals
- Create snapshots as needed to allow staff to go back in time
- Create file archives that allow users to roll back in case of a disaster.
EDpCloud for data delivery
EDpCloud continuously syncs file changes as they occur to one or more locations and from one or more locations to other locations.
EDpCloud pause and resume when combined with snapshots will protect against ransomware and will manage resource use and to automate the work flow as needed.
EDpCloud is available for the following operating systems:
- Linux
- Mac
- Windows
- Solaris on SPARC
- Solaris x86
- AIX
- Other UNIX OS’s as requested.
Users can mirror and backup data with EDpCloud, from any platform to any other platform. For example, system administrators can configure EDpCloud to synchronize data from windows, Linux, Mac to other Linux servers in other branch offices. As data changes in other branch offices, the software sends file changes in real-time to other branch offices for data protection.
In case of a disaster, the data is available from the other sites or servers without the need to restore.
Try EDpCloud now
Download EDpCloud or call a support Engineer at 952-746-4160 to discuss your disaster tolerance options!
Download now!
Contact EnduraData support now.References:
[1] AV-Test [2] Kapersky [3] A. A. El Haddi (I adapted these terms from my thesis in October, 1983). [4] https://www.forbes.com/sites/leemathews/2018/03/30/boeing-is-the-latest-wannacry-ransomware-victim/ [5] https://gcn.com/articles/2018/03/23/atlanta-ransomware.aspx [6] http://coastalcourier.com/section/2/article/91246/ [7] http://www.wdbj7.com/content/news/Police-investigating-potentially-compromised-files-at-United-Way-476172523.html [8] http://www.wsmv.com/story/36798130/city-of-spring-hill-computer-system-hit-by-ransomware [9] https://www.scmagazine.com/hbo-breach-accomplished-with-hard-work-by-hacker-poor-security-practices-by-victim/article/680568/ [10] https://www.healthdatamanagement.com/news/erie-county-medical-center-anatomy-of-a-ransomware-attack [11] https://www.telegraph.co.uk/news/2017/06/27/ukraine-hit-massive-cyber-attack1/ [12] http://www.cpapracticeadvisor.com/news/12391511/the-10-biggest-cyber-attacks-of-2017 [13] https://blog.barkly.com/10-million-dollar-ecmc-hospital-ransomware-attack [14] https://blog.barkly.com/2018-cybersecurity-statisticsRecent updates to the article
4/12/2018:
A day after we published this article:
Vanderbilt University researcher’s claim breaches linked to patient deaths.
https://www.scmagazineuk.com/vanderbilt-university-researchers-claim-breaches-linked-to-patient-deaths/article/753905/

Share this Post