WannaCry ransomware: The costs and the aftermath
By Nicole P, an EnduraData communications specialist
Ransomware: Do you have a data protection plan in place?
An unparalleled global outbreak of an incident of ransomware has taken the world by storm, causing significant data loss and upsetting home users and businesses alike. In the first installment of this article, we will discuss the basics surrounding the WannaCry malware. Later, in part two, we will go over who its victims were, the costs associated with it, and what is being done to fix it.
What is WannaCry Ransomware?
WannaCry is ransomware that was released in Europe on May 12, 2017, and attacked organizations and people who were using out-of-date versions of Windows [2]. Thus far, it has spread to over 150 countries worldwide and has claimed over 300,000 victims. Upon infection, victims were ordered to pay a ransom of $300 to $600 to recover their data. If the victim refused to pay within the timeframe given, the attackers threatened to delete the encrypted files permanently [1], resulting in data loss.
WannaCry is an encryption-based malware, which means that hackers first generate encrypted replicas of their victims’ files and then delete the original copies. The victims are then left with the encrypted files and must buy a decryption key prior to being allowed access to their own data. The ransomware was also designed in a way that pressures its victims into paying the hackers by gradually upping the payoff amount and threats of lost data at preset times [3].
Lastly, WannaCry is a worm in addition to being a malware program. When a worm gets into devices, it looks for other devices to infect and to make itself as far-reaching as possible. Being both a worm and malware explains how the infection spread so rapidly across the globe [9].
[ Try a copy of EDpCloud software today ]
Where and how did WannaCry ransomware start?
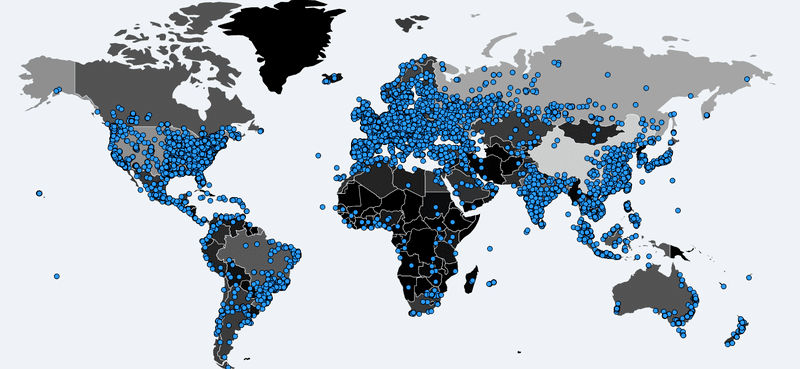
While security researchers cannot say for sure who released the ransomware, they do have ideas regarding the origins of the malware. The ransomware’s theft was first reported in April after it was published by a group who call themselves the “Shadow Brokers.” Not much is known about the Shadow Brokers but the group is believed to have Russian ties [1]. Although a specific starting point is currently unknown, it is alleged to have originated somewhere in Europe, most likely in the U.K. Security researchers believe that an email containing the ransomware was opened and subsequently infected hundreds of thousands of devices worldwide [5]. This map shows how the ransomware spread across the globe [11].
The exploit used in the WannaCry attack, codenamed EternalBlue, was stolen from the US National Security Agency (NSA) and was designed to take advantage of a vulnerability in older versions of Windows’ SMB/CIFS system. The SMB is a file-sharing system that usually operates on closed networks but can be manipulated if/when a device is linked to a public network [3].
One month prior to the theft of EternalBlue, a patch was released by Microsoft that was intended to fix the vulnerability, however, not enough people took advantage of it. The reason why is because there is a mentality that if the technology is functioning properly, it does not need maintenance or updates [2].
Organizations without effective data protection suffered the most.
Why has WannaCry been so successful?
Besides neglecting to utilize the patch, the success of the attack has been attributed to the fact that many organizations, especially in the healthcare and telecom industries, use obsolete technology that no longer gets updates, also known as “legacy software” [2].
Large organizations regularly use legacy software because their size makes software upgrades expensive and laborious. As a result, many large corporations made no effort to update or patch their systems due to their complexity and age. Consequently, the lack of updated software put those businesses at the highest risk of being infected and attacked[2] and of data loss.
Furthermore, by the time some organizations shift from legacy software to newer systems, modern technology is out-of-date because it can take years for vendors and organizations to meet specific regulations and agreements [2].
Additionally, both hardware and software vendors generally neglect to plan for future security failings and sell organizations costly systems that ultimately will not be able to accept patches. As such, the older the operating systems are, the more likely it is to be infected by malware and viruses specifically designed to target them [2]. Although this may not be true for some open-source operating systems such as Linux or other UNIX variants[13]
Although the U.S. government mostly evaded WannaCry, it currently uses technology that is at least decades old. And while $20 billion is spent on upgrading legacy technology, over $60 billion is spent on maintaining it. In fact, programmers are sometimes paid more by various government agencies to learn legacy computer languages just so they can keep the outdated systems running; all of which demonstrate the difficulty large organizations face to update their technology [2].
Part Two of WannaCry
Who/where was attacked?
WannaCry is being hailed as the largest ransomware outbreak known to date, hitting the U.S., Asia, and Europe. In the week following the initial attack, the Department of Homeland Security (DHS) reported that the number of victims in the U.S. was small. The only major company known to affected in the U.S. was FedEx [1] [4]. The DHS did note that the full extent of the attack was not yet fully known since variations of the malware were still coming out [1].
The loss of data knows no boundaries
Of the countries in Asia that were attacked, China, India, and Japan have reported major interruptions. In China, many computers run a bootlegged version of Microsoft, and thus the software patch was not accessible to a large portion of the population. China officials said that over 40,000 organizations and establishments have been hit by the ransomware in the county, including PetroChina—one of China’s biggest oil companies. Additionally, students at one of the country’s top universities were unable to access their files which caused major interruptions to regular class and test schedules [1].
In Japan, various well-known manufacturers such as Hitachi and Nissan were attacked by WannaCry. As a result, Hitachi lost email access and lesser important functionalities. In India, electric companies as well as over 100 of the country’s law enforcement agencies’ systems were infected [1].
Europe was hit the hardest, with the U.K. reporting its health care system being attacked on the first day the malware was released. The National Health System (NHS) could not provide basic healthcare services because patient files were inaccessible. Consequently, hospitals were closed and non-emergency surgeries and appointments were canceled [5]. According to the U.K. government, 48 of the 248 NHS organizations were infected in total [10]. It is unknown if any lives were lost as a result of disabled access to the healthcare systems.
Other European victims include French carmaker Renault, Germany’s train station systems, Spain’s Telefonica telecom company, and the central bank, government agencies, and railroads in Russia [5].
Information services management errors and no data protection
In Africa, Moroccan CERT security services, the ministry of agriculture and the ministry of higher education alerted institutions such as IAV Hassan II that they were extremely vulnerable to WannaCry.
What are the impacts of being attacked?
There were various consequences businesses and home users faced as a result of being attacked by WannaCry including:
- Short-term or permanent loss of confidential and/or patented data
- Interruption to business operations
- Damage to the organization’s reputation
- Financial damages sustained to reestablish systems and archives [8].
What are the costs associated with the attack?
Due to the unprecedented success of WannaCry, experts agree that 2017 is likely to be the worst year for malware attacks to date. Cybersecurity Ventures, a market researcher, said ransomware costs were $1.5 billion in 2016 but it has been estimated that the total costs associated with the WannaCry attack could reach $4 billion [4].
If regular backups are not a part of an organization’s data protection plan, paying the ransom is usually the only way to get the data back. Hackers generally decrypt the information upon receiving the ransom, however, the victim is then placed on a list of organizations who are known to pay and are then considered easy targets [3].
Although ransom costs for organizations could be severe, thus far, hackers are known to have only made approximately $100,000 in Bitcoin ransoms [4] [6]. Researchers believe the fees for restoration and lost productivity are likely to be far greater than the actual ransom costs incurred. In fact, many businesses such as Nissan, NHS, and Hitachi refused to pay the ransom and used their backups and additional resources to recuperate instead [4] [6].
Besides companies’ outright refusal to pay, hackers made several fatal flaws while designing the malware that contributed to less financial gains for themselves. First, they neglected to provide a way to trace ransom payments back to the payees. Without a means to trace the payments, organizations that normally would have paid the ransom were hesitant because there was no guarantee they would get their information back. Second, the hackers demanded the ransom to be paid in an online currency known as Bitcoin. Many organizations do not know how to use Bitcoins and even if they do, the process of getting and setting up Bitcoin exchange can take weeks [5].
How to stop Malware Attacks
Since malware can be purchased without much difficulty on the darknet, ransomware attacks have and will continue to happen frequently [3]. As such, there are a variety of ways that organizations can protect themselves from becoming victims. Microsoft’s security experts advise all Windows users to perform software updates and install the patch issued. Other measures include:
- Deactivate SMBv1 to stop the spread of WannaCry within the computer’s network [1]
- Perform regular backups [1]
- Install and run antivirus software [1]
- Do not open emails from unknown senders [1]
- Use automated updates to ensure the software is current [1]
- Use the “Show file extensions” feature in Windows and do not open files using “.exe.,” “.vbs” and “.scr.” [1]
- Shut down Internet and Wifi connections if an issue is detected [1]
- Report ransomware attacks to law enforcement agencies [8]
- Use only trusted sites when downloading software [8]
- Use disaster tolerance and disaster escape technologies[13]
- Backup to Linux systems[13]
- Leverage real-time archival and snapshots[13]
Despite there being a variety of ways to protect against becoming a malware victim, the WannaCry attack is a reminder of how devastating human errors such as opening infected attachments and neglecting to perform software updates can be. In 2016, an estimated $73 billion was spent on cybersecurity, according to the research firm IDC, but it was human errors and not a lack of protection that led to the rapid spread of the ransomware [10].
Besides organizations being more aware of how human errors contribute to attacks, industries need to be more cognizant of the importance of working together to fight against ransomware infections. Microsoft’s president, Brad Smith, posted a company blog on the Monday following the attack that called for the technology industry and intercontinental governments to work collectively to halt the exploitation of digital vulnerabilities. Furthermore, while the leakage of software from the NSA was unacceptable and dangerous, it was not surprising since ransomware attacks will only continue to grow [7].
The Chipotle combined attack
In a statement given by Chipotle officials on May 26, 2017, the popular chain admitted that their point of sales systems was infected by ransomware. The attack was also used to steal patrons’ payment information from a large majority of their establishments over the course of three weeks.
Between March 24 and April 18, nearly all its 2,250 restaurants were targeted by hackers, including some of its Canadian locations. Even though the ransomware has been eradicated, the hackers were able to steal information such as verification codes and account numbers. The stolen data could potentially be used for various criminal activities such as online purchases, the creation of cloned credit cards, and/or to empty debit card-linked accounts.
The admission of the recent infection will likely jeopardize the company’s sales once more. The chain has only recently recovered from its 2015 incident in which hundreds of customers had fallen ill due to various disease outbreaks linked to the chain.
Attackers obtained the information from the magnetic strips on the cards but customers were not informed of the breach immediately because Chipotle did not have the patrons’ names and addresses. Despite a press release that was posted on the company’s website to warn customers, lawyers for those impacted claim the franchise did not do enough to inform the patrons. Chipotle refused to comment further [12].
[ Contact EnduraData Enginners]
Related articles
References
- Chappell, Bill (15 May 2017). “WannaCry Ransomware: What We Know Monday”. NPR. Retrieved 17 May 2017.
- Larson, Selena (17 May 2017). “Why WannaCry ransomware took down so many businesses”. CNN. Retrieved 17 May 2017.
- Woollaston, Victoria (22 May 2017). “WannaCry ransomware: what it is and how to protect yourself”. Wired. Retrieved 22 May 2017.
- Berr, Jonathan (16 May 2017). “’ WannaCry’ ransomware attack losses could reach $4 billion”. CBS News. Retrieved 17 May 2017.
- Kharpla, Arjun (15 May 2017). “Hackers who infected 200,000 machines have only made $50,000 worth of bitcoin”. CNBC. Retrieved 17 May 2017.
- Mozur, P., Scott, M. & Goel, V. (19 May 2017). “Victims Call Hackers’ Bluff as Ransomware Deadline Nears”. The New York Times. Retrieved 19 May 2017.
- Reed, Ryan (15 May 2017). “WannaCry: What You Need to Know About Global Ransomware Attack”. Rolling Stone. Retrieved 18 May 2017.
- “Indicators Associated with WannaCry Ransomware”. (19 May 2017). Department of Homeland Security. Retrieved 25 May 2017.
- Knowles, Jamillah (13 May 2017). “Factbox: Don’t click – What is the ‘ransomware’ WannaCry worm?” Reuters. Retrieved 25 May 2017.
- Dwoskin, E. & Adam, K. (14 May 2017). “More than 150 countries affected by a massive cyberattack, Europol says”. The Washington Post. Retrieved 25 May 2017.
- Ashkenas, J. & Pearce, A. (12 May 2017). “Animated Map of How Tens of Thousands of Computers Were Infected With Ransomware”. The New York Times. Retrieved 17 May 2017.
- “Chipotle Says Hackers Hit Most Restaurants in Data Breach”. (27 May 2017). Reuters. Retrieved 30 May 2017.
Relevant new links:
- https://www.npr.org/sections/thetwo-way/2017/05/15/528451534/wannacry-ransomware-what-we-know-monday
- https://money.cnn.com/2017/05/17/technology/wannacry-ransomware-business-security/
- https://www.wired.co.uk/article/wannacry-ransomware-virus-patch
- https://www.cbsnews.com/news/wannacry-ransomware-attacks-wannacry-virus-losses/
- https://www.cnbc.com/2017/05/15/wannacry-ransomware-hackers-have-only-made-50000-worth-of-bitcoin.html
- https://www.nytimes.com/2017/05/19/business/hacking-malware-wanncry-ransomware-deadline.html
- https://www.rollingstone.com/culture/news/wannacry-what-you-need-to-know-about-global-ransomware-attack-w482268
- https://www.us-cert.gov/ncas/alerts/TA17-132A
- https://www.reuters.com/article/us-britain-security-hospitals-ransomware-idUSKBN1882O2
- https://www.washingtonpost.com/business/economy/more-than-150-countries-affected-by-massive-cyberattack-europol-says/2017/05/14/5091465e-3899-11e7-9e48-c4f199710b69_story.html?utm_term=.1477f95d2cc7
- https://www.nytimes.com/interactive/2017/05/12/world/europe/wannacry-ransomware-map.html?_r=1
- https://www.ndtv.com/world-news/most-of-chipotle-branches-hit-by-the-wannacry-cyber-attack-1704561
- A. El Haddi (2016)“Move to Linux, OpenBSD or you will continue to pay the price”. EnduraData, “Personal communication”.
Share this Post